AirLift is a Pakistani decentralized urban mass transit startup backed by San Francisco-based First Round Capital, which also is an Uber investor. It, in fact, is the world’s first decentralized mass transit system. Led by Huynh Chen and Sarmad Khan, PrivacySavvy’s research team discovered a major security bug in its premium grocery service Airlift Express. With hundreds of orders every day, Airlift Express is quickly becoming a widely-used eCommerce company.
The company quickly responded to our report and fixed OTP vulnerability alongside other security issues. Still, this AirLift’s eCommerce OTP vulnerability is a good reminder of why OTPs are not enough for your accounts’ security today.
Modern brute force attackers are sophisticated but unfortunately, the technology required to repel them is not. OTPs (One-time passwords) were introduced as a convenient means of identifying and authenticating users. Still, this intention was defeated not too long after its introduction; hackers found a way around it. But companies keep using them.
According to PrivacySavvy security lab, OTPs are no longer considered secure because of the heavy brute force attack witnessed in recent times.
OTPs sent via SMS were developed to prevent replay attacks and add an extra layer of log-on security. How this works is that the website sends a unique code to a user through text, the one-time code sent is inputted in the space provided along with a username and password combination. Upon verifying the OTP’s authenticity, the user is then allowed to authorize a transaction or access a site. While this may sound simple and secure in theory, it’s a different case in reality. That’s precisely what this report is going to prove today.
How brute-force attack works
Brute force attack remains a nightmare for web developers; it is undoubtedly one of the most popular password-cracking methods known to man. But beyond cracking passwords, they also reveal hidden web pages and contents in a web application. Unfortunately, thousands of internet users are being exposed to brute force attacks daily.
In a typical brute force attack, the attacker tries cracking the password using a series of combination of letters and numbers until he gets its right. It is more of a ‘try until you get it’ approach. This could range from a few minutes to a few hours (depending on how long it takes to crack a particular password).
The AirfLift Express’s OTP and brute force
PrivacySavvy reporters observed this with AirLift Express, an eCommerce platform where customers order medicines, groceries, and other essential items.
As seen in the screenshot below, a user tried accessing his account but forgot his password. When this happens, AirLift Express advises you to click on forgot password. After this, the user enters his phone number or email address with which he opened the account.
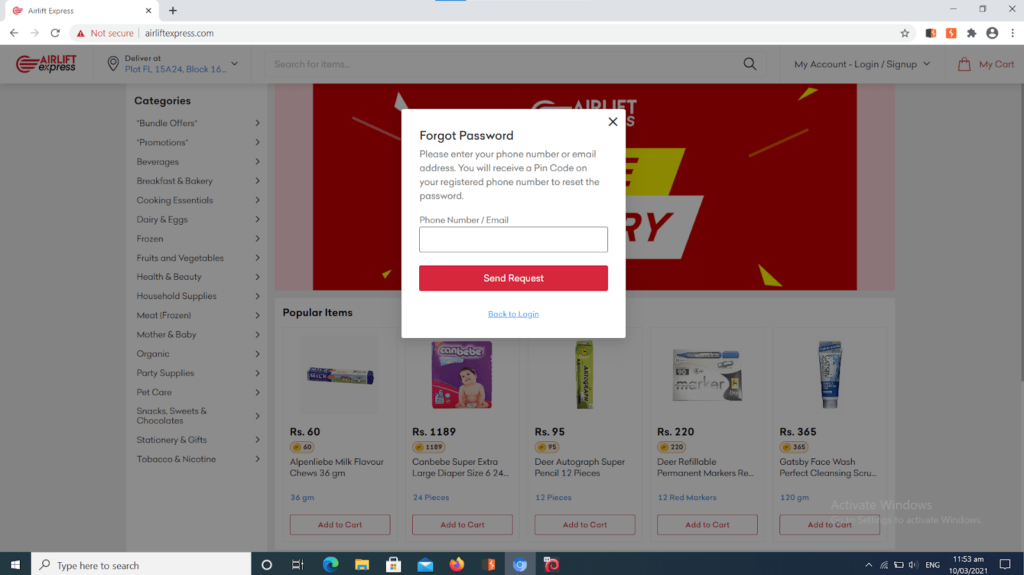
Below, we see AirLift Express sends a unique OTP code which the user then inputs in the provided box.
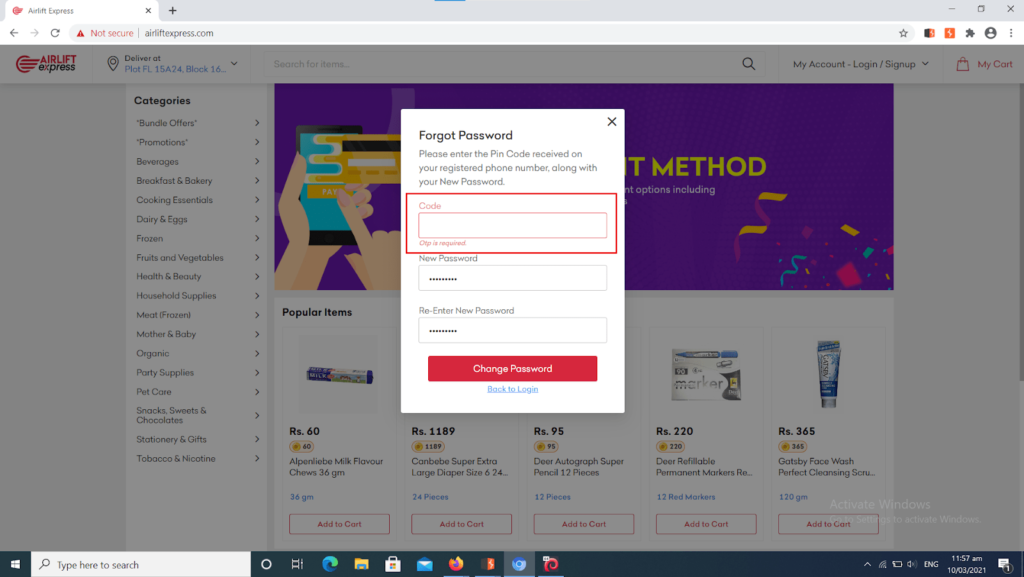
It’s when things get risky for users. Here, a hacker can input a legit mobile number (which any skilled security person can get easily via social engineering) and could brute force the OTP code while trying out multiple combinations of numbers. Our researchers did it as an illustration of the vulnerability as you can see in the screenshots below:
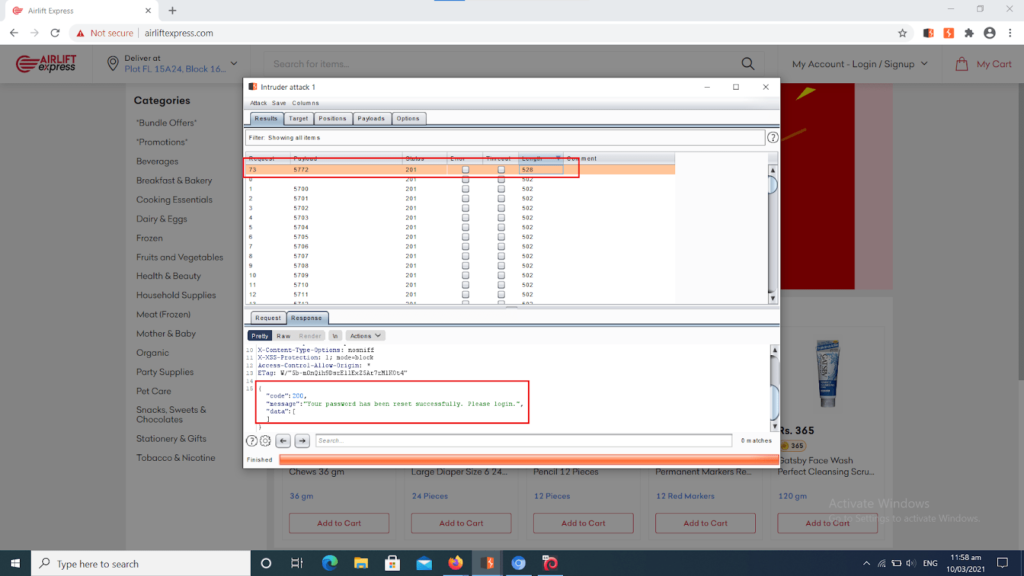
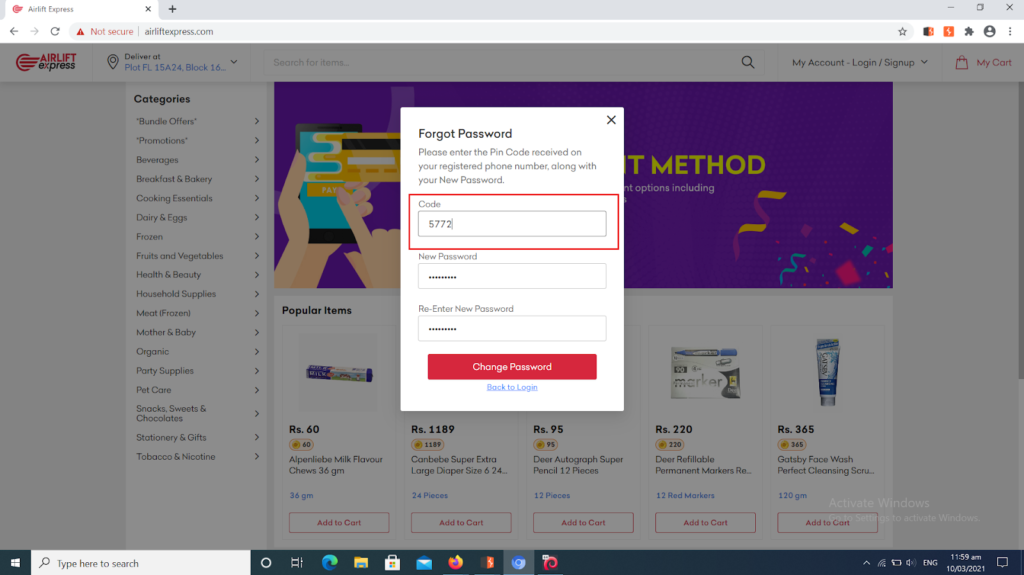
The hacker then keeps trying various combinations until he finally gets it right (our researchers got it right within 7 minutes in the case of Airlift Express). Once he achieves this, he takes over the user’s account to perform all sorts of fraudulent acts.
PrivacySavvy’s security team’s close observation of events shows there are several types of tools employed for these brute-force attacks ranging from aircrack-ng, john the ripper, rainbow crack L0phtCrack, Ophcrack, Hashcat, DaveGrohl, Ncrack, and THC Hydra.
Why OTPs over text are vulnerable
To further give light to the issue, our security team consulted a research paper published in 2013 and written by researchers at Northeastern University and Technische Universitat Berlin titled “SMS-Based One-Time Passwords: Attacks and Defense.” The report takes a comprehensive but in-depth look at OTP vulnerability.
After analyzing the security structure of OTP via text and studying recent brute force attacks, all those researchers agree that OTPs via SMS is no longer secure for two significant reasons:
- OTPs via SMS is built on two foundations; mobile devices and cellular networks. Back then (in 2013), users could trust that these two foundations will keep their promise of confidentiality, security, and privacy, but this is no longer the case. These two sectors have broken their promises repeatedly in the past, thereby exposing users to brute-force attacks.
- In recent times, hackers and brute-force attackers have developed unique Trojans that can bypass OTP over SMS security. These trojans take over mobile devices, and ever since this has been the case, no one has offered a solution or studied this security vulnerability, the paper reports.
But beyond the report, OTP vulnerability has become more popular in the wake of recent security breaches. Given this, seasoned security experts have advised that there is a need for tight security measures and multiple authentications; unfortunately, many companies have ignored this call.
What’s the better alternative and solution to OTP vulnerabilities
Multi-factor authentication offers more security than a simple username and password combinations. That is so because the user must meet specific requirements, usually a) username/password b) have a mobile device; sometimes, a third authentication is needed, too.
Multi-factor authentication is not a new initiative. For instance, ATMs require a two-factor authentication; first, you will need a card, and then you will need a PIN. Lots of websites, including banks, are beginning to adopt OTP over SMS.
However, many companies do not understand that multi-factor authentication has many sides, and not all are safe.
There are more safe ways to approach multi-factor authentication to make it securer than just an OTP over SMS. One of such is verification using a physical token or mobile app.
Another way to secure users’ accounts is that developers can lock out accounts after a given number of unsuccessful attempts; this lockout could be for a certain period.
Furthermore, web developers, companies, and institutions can protect their clients from brute-force attacks using Captcha. Fortunately for users in Pakistan, Airlift has taken care of this OTP brute force vulnerability in their online grocery shopping service Airlift Express. Below is a part of their final statement sent to the PrivacySavvy research team via email confirming the fix:
We have been moving very quickly in development and fixing. Multiple security patches have gone into production. The vulnerabilities shared by you are pushed to production. Thanks for this. You can share the report on this bug.
But as illustrated above, hackers can hack into the users’ accounts of any mobile or web-based app having OTP authentication without any additional rules set.
About our research Lab
At PrivacySavvy, our focus is to contribute towards a world with the least-possible cyber threats. Our fast-growing research lab has the best security researchers who are always on the lookout for users to guard themselves against ever-present cyber threats. But beyond individuals, we also focus on helping companies protect the data of their users.
